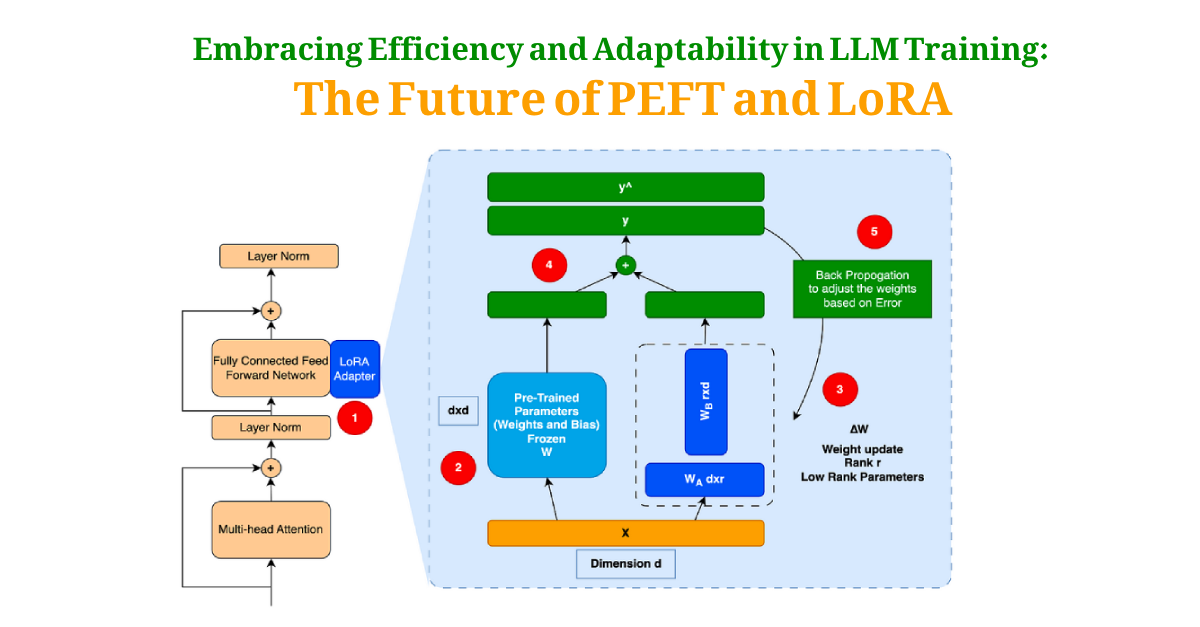
Introduction: Large Language Models (LLMs) like GPT (Generative Pre-trained Transformer) have revolutionized the field of natural language processing (NLP). These models have an extraordinary ability […]
Author: Farrukh Naveed Anjum
How to Avoid Getting Your Servers Hacked
In today’s digitized world, server security is paramount. As cyber threats become more sophisticated, ensuring the security of your server is crucial to protect sensitive […]
Developers vs. QC: A Friendly Feud in the Tech Jungle
In the mysterious realms of the tech jungle, two species coexist in a unique harmony: the Software Developers (known in layman’s terms as “Code Wizards”) […]
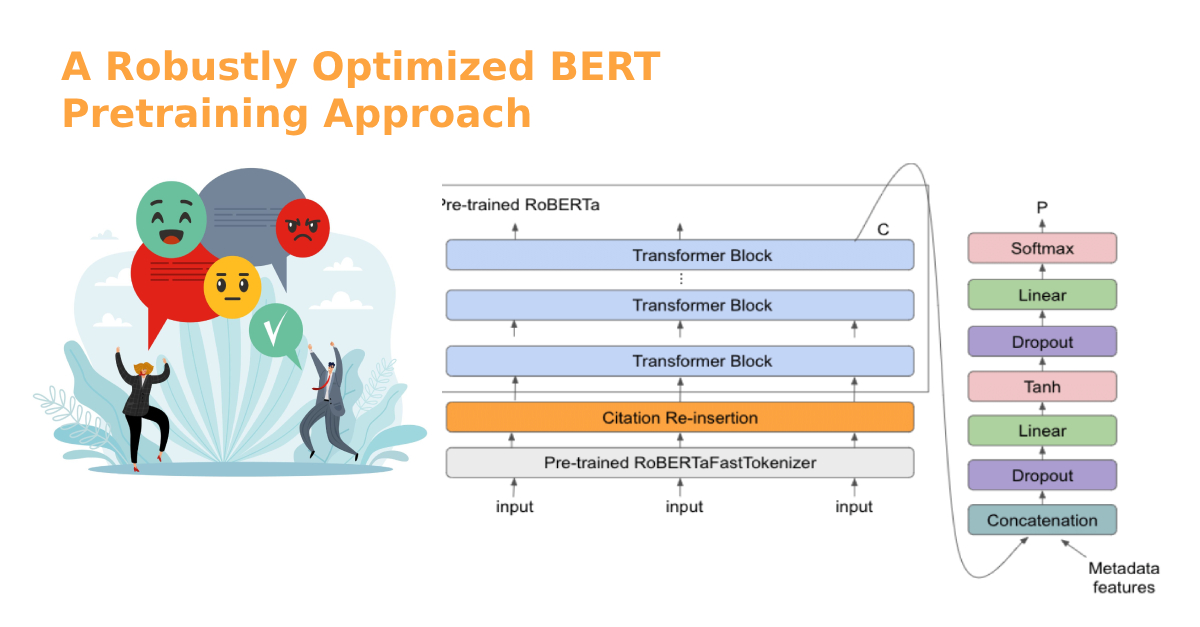
A Robustly Optimized BERT Pretraining Approach hands on using Python
ROBERTa stands for “A Robustly Optimized BERT Pretraining Approach.” This is a model created by Facebook’s AI team, and it’s essentially an optimization of BERT […]
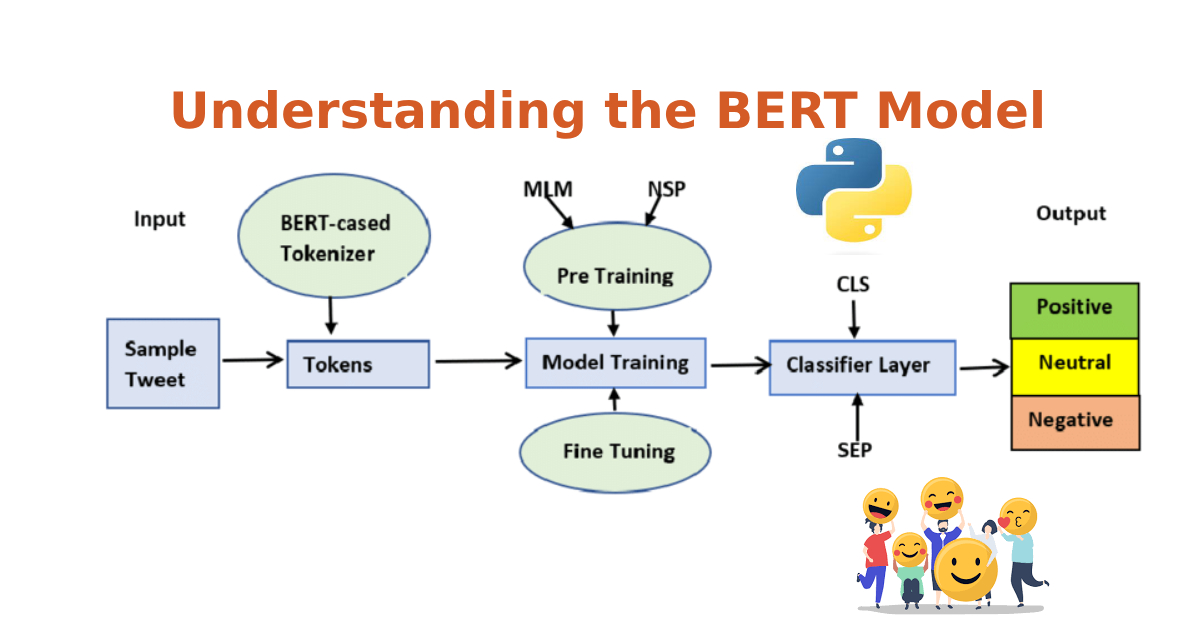
Understanding the BERT Model
BERT, which stands for Bidirectional Encoder Representations from Transformers, has revolutionized the world of natural language processing (NLP). Developed by researchers at Google in 2018, […]
Architectural Design Patterns in Microservices using Python
In today’s software development landscape, microservices architecture has emerged as a dominant pattern to build scalable, maintainable, and agile applications. Unlike monolithic architectures, where an […]
Large Language Models: History, Current Works, and Research Areas
Introduction Large Language Models (LLMs) have emerged as cornerstones of modern Natural Language Processing (NLP). From early statistical models to the sophisticated deep learning architectures […]
Fine-tuning GPT-3’s LLM Model with PEFT on Elasticsearch Data using Python
OpenAI’s GPT-3, particularly its LLM (Language Model) variant, has been a game-changer in the world of natural language processing. Many companies and individual developers are […]
Ansible: A Primer, Installation, and Deploying 500 Docker Containers
Ansible is an open-source automation tool, used for configuration management, application deployment, and task automation. Unlike other management tools, Ansible uses an agentless architecture, relying […]
Assessing the Future Security of Cryptocurrencies
How much Compute is Required to Crack 12 Words Wallet of Bitcoin ?In the context of Bitcoin and many other cryptocurrencies, the 12-word mnemonic phrase […]